Official 2014 Latest Cisco 640-554 Dump Free Download(11-20)!
QUESTION 11
Which four tasks are required when you configure Cisco IOS IPS using the Cisco Configuration Professional IPS wizard? (Choose four.)
A. Select the interface(s) to apply the IPS rule.
B. Select the traffic flow direction that should be applied by the IPS rule.
C. Add or remove IPS alerts actions based on the risk rating.
D. Specify the signature file and the Cisco public key.
E. Select the IPS bypass mode (fail-open or fail-close).
F. Specify the configuration location and select the category of signatures to be applied to the selected
interface(s).
Answer: ABDF
QUESTION 12
Which statement is a benefit of using Cisco IOS IPS?
A. It uses the underlying routing infrastructure to provide an additional layer of security.
B. It works in passive mode so as not to impact traffic flow.
C. It supports the complete signature database as a Cisco IPS sensor appliance.
D. The signature database is tied closely with the Cisco IOS image.
Answer: A
QUESTION 13
Which description of the Diffie-Hellman protocol is true?
A. It uses symmetrical encryption to provide data confidentiality over an unsecured communications channel.
B. It uses asymmetrical encryption to provide authentication over an unsecured communications channel.
C. It is used within the IKE Phase 1 exchange to provide peer authentication.
D. It provides a way for two peers to establish a shared-secret key, which only they will know, even though
they are communicating over an unsecured channel.
E. It is a data integrity algorithm that is used within the IKE exchanges to guarantee the integrity of the
message of the IKE exchanges.
Answer: D
QUESTION 14
Which IPsec transform set provides the strongest protection?
A. crypto ipsec transform-set 1 esp-3des esp-sha-hmac
B. crypto ipsec transform-set 2 esp-3des esp-md5-hmac
C. crypto ipsec transform-set 3 esp-aes 256 esp-sha-hmac
D. crypto ipsec transform-set 4 esp-aes esp-md5-hmac
E. crypto ipsec transform-set 5 esp-des esp-sha-hmac
F. crypto ipsec transform-set 6 esp-des esp-md5-hmac
Answer: C
QUESTION 15
Which two options are characteristics of the Cisco Configuration Professional Security Audit wizard? (Choose two.)
A. displays a screen with fix-it check boxes to let you choose which potential security-related configuration
changes to implement
B. has two modes of operation: interactive and non-interactive
C. automatically enables Cisco IOS firewall and Cisco IOS IPS to secure the router
D. uses interactive dialogs and prompts to implement role-based CLI
E. requires users to first identify which router interfaces connect to the inside network and which connect to
the outside network
Answer: AE
QUESTION 16
Which statement describes a result of securing the Cisco IOS image using the Cisco IOS image resilience feature?
A. The show version command does not show the Cisco IOS image file location.
B. The Cisco IOS image file is not visible in the output from the show flash command.
C. When the router boots up, the Cisco IOS image is loaded from a secured FTP location.
D. The running Cisco IOS image is encrypted and then automatically backed up to the NVRAM.
E. The running Cisco IOS image is encrypted and then automatically backed up to a TFTP server.
Answer: B
QUESTION 17
Which aaa accounting command is used to enable logging of the start and stop records for user terminal sessions on the router?
A. aaa accounting network start-stop tacacs+
B. aaa accounting system start-stop tacacs+
C. aaa accounting exec start-stop tacacs+
D. aaa accounting connection start-stop tacacs+
E. aaa accounting commands 15 start-stop tacacs+
Answer: C
QUESTION 18
Which access list permits HTTP traffic sourced from host 10.1.129.100 port 3030 destined to host 192.168.1.10?
A. access-list 101 permit tcp any eq 3030
B. access-list 101 permit tcp 10.1.128.0 0.0.1.255 eq 3030 192.168.1.0 0.0.0.15 eq www
C. access-list 101 permit tcp 10.1.129.0 0.0.0.255 eq www 192.168.1.10 0.0.0.0 eq www
D. access-list 101 permit tcp host 192.168.1.10 eq 80 10.1.0.0 0.0.255.255 eq 3030
E. access-list 101 permit tcp 192.168.1.10 0.0.0.0 eq 80 10.1.0.0 0.0.255.255
F. access-list 101 permit ip host 10.1.129.100 eq 3030 host 192.168.1.100 eq 80
Answer: B
QUESTION 19
Which location is recommended for extended or extended named ACLs?
A. an intermediate location to filter as much traffic as possible
B. a location as close to the destination traffic as possible
C. when using the established keyword, a location close to the destination point to ensure that return traffic
is allowed
D. a location as close to the source traffic as possible
Answer: D
QUESTION 20
Which statement about asymmetric encryption algorithms is true?
A. They use the same key for encryption and decryption of data.
B. They use the same key for decryption but different keys for encryption of data.
C. They use different keys for encryption and decryption of data.
D. They use different keys for decryption but the same key for encryption of data.
Answer: C
If you want to pass the Cisco 640-554 Exam sucessfully, recommend to read latest Cisco 640-554 Dump full version.

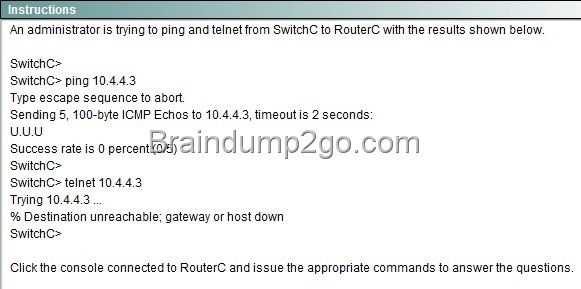
![clip_image001[4] clip_image001[4]](http://examgod.com/l2pimages/Free2014LatestCisco200120Dump161170Downl_9A18/clip_image0014_thumb.jpg)
![clip_image001[6] clip_image001[6]](http://examgod.com/l2pimages/Free2014LatestCisco200120Dump161170Downl_9A18/clip_image0016_thumb.jpg)
![clip_image001[8] clip_image001[8]](http://examgod.com/l2pimages/Free2014LatestCisco200120Dump161170Downl_9A18/clip_image0018_thumb.jpg)
![clip_image001[10] clip_image001[10]](http://examgod.com/l2pimages/Free2014LatestCisco200120Dump161170Downl_9A18/clip_image00110_thumb.jpg)
![clip_image001[12] clip_image001[12]](http://examgod.com/l2pimages/Free2014LatestCisco200120Dump161170Downl_9A18/clip_image00112_thumb.jpg)
![clip_image001[14] clip_image001[14]](http://examgod.com/l2pimages/Free2014LatestCisco200120Dump161170Downl_9A18/clip_image00114_thumb.jpg)
![clip_image001[16] clip_image001[16]](http://examgod.com/l2pimages/Free2014LatestCisco200120Dump161170Downl_9A18/clip_image00116_thumb.jpg)
![clip_image001[18] clip_image001[18]](http://examgod.com/l2pimages/Free2014LatestCisco200120Dump161170Downl_9A18/clip_image00118_thumb.jpg)
![clip_image001[20] clip_image001[20]](http://examgod.com/l2pimages/Free2014LatestCisco200120Dump161170Downl_9A18/clip_image00120_thumb.jpg)
![clip_image001[22] clip_image001[22]](http://examgod.com/l2pimages/Free2014LatestCisco200120Dump161170Downl_9A18/clip_image00122_thumb.jpg)
![clip_image001[24] clip_image001[24]](http://examgod.com/l2pimages/Free2014LatestCisco200120Dump161170Downl_9A18/clip_image00124_thumb.jpg)
![clip_image001[26] clip_image001[26]](http://examgod.com/l2pimages/Free2014LatestCisco200120Dump161170Downl_9A18/clip_image00126_thumb.jpg)
![clip_image001[28] clip_image001[28]](http://examgod.com/l2pimages/Free2014LatestCisco200120Dump161170Downl_9A18/clip_image00128_thumb.jpg)
![clip_image001[30] clip_image001[30]](http://examgod.com/l2pimages/Free2014LatestCisco200120Dump161170Downl_9A18/clip_image00130_thumb.jpg)
![clip_image001[32] clip_image001[32]](http://examgod.com/l2pimages/Free2014LatestCisco200120Dump161170Downl_9A18/clip_image00132_thumb.jpg)
![clip_image001[34] clip_image001[34]](http://examgod.com/l2pimages/Free2014LatestCisco200120Dump161170Downl_9A18/clip_image00134_thumb.jpg)
![clip_image001[36] clip_image001[36]](http://examgod.com/l2pimages/Free2014LatestCisco200120Dump161170Downl_9A18/clip_image00136_thumb.jpg)
![clip_image001[38] clip_image001[38]](http://examgod.com/l2pimages/Free2014LatestCisco200120Dump161170Downl_9A18/clip_image00138_thumb.jpg)
![clip_image001[40] clip_image001[40]](http://examgod.com/l2pimages/Free2014LatestCisco200120Dump161170Downl_9A18/clip_image00140_thumb.jpg)
![clip_image001[42] clip_image001[42]](http://examgod.com/l2pimages/Free2014LatestCisco200120Dump161170Downl_9A18/clip_image00142_thumb.jpg)
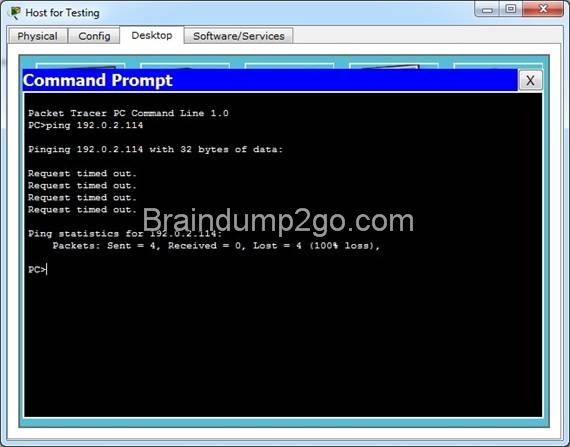
![clip_image002[4] clip_image002[4]](http://examgod.com/l2pimages/Free2014LatestCisco200120Dump161170Downl_9A18/clip_image0024_thumb.jpg)
![clip_image002[6] clip_image002[6]](http://examgod.com/l2pimages/Free2014LatestCisco200120Dump161170Downl_9A18/clip_image0026_thumb.jpg)
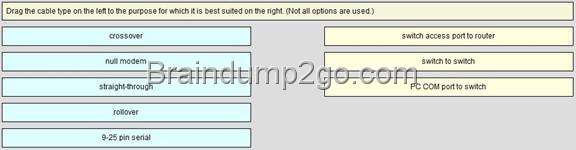
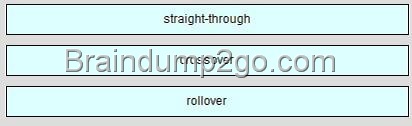
![clip_image002[4] clip_image002[4]](http://examgod.com/l2pimages/Free2014LatestCisco200120Dump151160Downl_8FE8/clip_image0024_thumb.jpg)
![clip_image001[4] clip_image001[4]](http://examgod.com/l2pimages/Free2014LatestCisco200120Dump151160Downl_8FE8/clip_image0014_thumb.jpg)
![clip_image002[6] clip_image002[6]](http://examgod.com/l2pimages/Free2014LatestCisco200120Dump151160Downl_8FE8/clip_image0026_thumb.jpg)
![clip_image001[6] clip_image001[6]](http://examgod.com/l2pimages/Free2014LatestCisco200120Dump151160Downl_8FE8/clip_image0016_thumb.jpg)
![clip_image002[8] clip_image002[8]](http://examgod.com/l2pimages/Free2014LatestCisco200120Dump151160Downl_8FE8/clip_image0028_thumb.jpg)
![clip_image001[8] clip_image001[8]](http://examgod.com/l2pimages/Free2014LatestCisco200120Dump151160Downl_8FE8/clip_image0018_thumb.jpg)
![clip_image002[10] clip_image002[10]](http://examgod.com/l2pimages/Free2014LatestCisco200120Dump151160Downl_8FE8/clip_image00210_thumb.jpg)
![clip_image001[10] clip_image001[10]](http://examgod.com/l2pimages/Free2014LatestCisco200120Dump151160Downl_8FE8/clip_image00110_thumb.jpg)
![clip_image002[12] clip_image002[12]](http://examgod.com/l2pimages/Free2014LatestCisco200120Dump151160Downl_8FE8/clip_image00212_thumb.jpg)
![clip_image001[12] clip_image001[12]](http://examgod.com/l2pimages/Free2014LatestCisco200120Dump151160Downl_8FE8/clip_image00112_thumb.jpg)
![clip_image002[14] clip_image002[14]](http://examgod.com/l2pimages/Free2014LatestCisco200120Dump151160Downl_8FE8/clip_image00214_thumb.jpg)
![clip_image001[14] clip_image001[14]](http://examgod.com/l2pimages/Free2014LatestCisco200120Dump151160Downl_8FE8/clip_image00114_thumb.jpg)
![clip_image002[16] clip_image002[16]](http://examgod.com/l2pimages/Free2014LatestCisco200120Dump151160Downl_8FE8/clip_image00216_thumb.jpg)
![clip_image002[20] clip_image002[20]](http://examgod.com/l2pimages/Free2014LatestCisco200120Dump151160Downl_8FE8/clip_image00220_thumb.jpg)
![clip_image002[24] clip_image002[24]](http://examgod.com/l2pimages/Free2014LatestCisco200120Dump151160Downl_8FE8/clip_image00224_thumb.jpg)
![clip_image002[26] clip_image002[26]](http://examgod.com/l2pimages/Free2014LatestCisco200120Dump151160Downl_8FE8/clip_image00226_thumb.jpg)
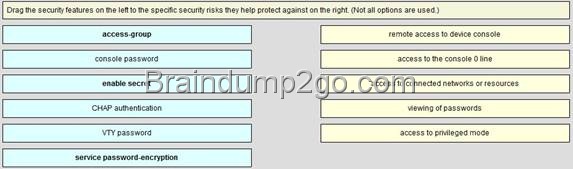

![clip_image002[4] clip_image002[4]](http://examgod.com/l2pimages/Free2014LatestCisco200120Dump141150Downl_8E94/clip_image0024_thumb.jpg)
![clip_image001[4] clip_image001[4]](http://examgod.com/l2pimages/Free2014LatestCisco200120Dump141150Downl_8E94/clip_image0014_thumb.jpg)
![clip_image001[4] clip_image001[4]](http://examgod.com/l2pimages/Free2014LatestCisco200120Dump131140Downl_8DA9/clip_image0014_thumb.jpg)
![clip_image001[6] clip_image001[6]](http://examgod.com/l2pimages/Free2014LatestCisco200120Dump131140Downl_8DA9/clip_image0016_thumb.jpg)
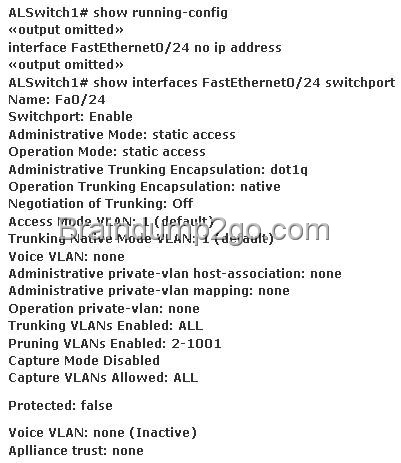
![clip_image001[4] clip_image001[4]](http://examgod.com/l2pimages/Free2014LatestCisco200120Dump121130Downl_8CCD/clip_image0014_thumb.jpg)
![clip_image001[6] clip_image001[6]](http://examgod.com/l2pimages/Free2014LatestCisco200120Dump121130Downl_8CCD/clip_image0016_thumb.jpg)
![clip_image001[8] clip_image001[8]](http://examgod.com/l2pimages/Free2014LatestCisco200120Dump121130Downl_8CCD/clip_image0018_thumb.jpg)