Free 2014 Latest Cisco 200-120 Dump (111-120) Download!
QUESTION 111
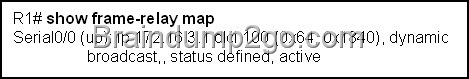
Refer to the exhibit. What is the meaning of the term dynamic as displayed in the output of the show frame-relay map command shown?
A. The Serial0/0 interface is passing traffic.
B. The DLCI 100 was dynamically allocated by the router.
C. The Serial0/0 interface acquired the IP address of 172.16.3.1 from a DHCP server.
D. The DLCI 100 will be dynamically changed as required to adapt to changes in the Frame Relay cloud.
E. The mapping between DLCI 100 and the end station IP address 172.16.3.1 was learned through Inverse ARP.
Answer: E
Explanation:
Inverse Address Resolution Protocol (Inverse ARP) was developed to provide a mechanism for dynamic DLCI to Layer 3 address maps. Inverse ARP works much the same way Address Resolution Protocol (ARP) works on a LAN. However, with ARP, the device knows the Layer 3 IP address and needs to know the remote data link MAC address. With Inverse ARP, the router knows the Layer 2 address which is the DLCI, but needs to know the remote Layer 3 IP address. When using dynamic address mapping, Inverse ARP requests a next-hop protocol address for each active PVC. Once the requesting router receives an Inverse ARP response, it updates its DLCI-to-Layer 3 address mapping table. Dynamic address mapping is enabled by default for all protocols enabled on a physical interface. If the Frame Relay environment supports LMI autosensing and Inverse ARP, dynamic address mapping takes place automatically. Therefore, no static address mapping is required.
QUESTION 112
A network administrator needs to configure a serial link between the main office and a remote location. The router at the remote office is a non-Cisco router. How should the network administrator configure the serial interface of the main office router to make the connection?
A. Main(config)# interface serial 0/0
Main(config-if)# ip address 172.16.1.1 255.255.255.252
Main(config-if)# no shut
B. Main(config)# interface serial 0/0
Main(config-if)# ip address 172.16.1.1 255.255.255.252
Main(config-if)# encapsulation ppp
Main(config-if)# no shut
C. Main(config)# interface serial 0/0
Main(config-if)# ip address 172.16.1.1 255.255.255.252
Main(config-if)# encapsulation frame-relay
Main(config-if)# authentication chap
Main(config-if)# no shut
D. Main(config)# interface serial 0/0
Main(config-if)#ip address 172.16.1.1 255.255.255.252
Main(config-if)#encapsulation ietf
Main(config-if)# no shut
Answer: B
Explanation:
With serial point to point links there are two options for the encapsulation. The default, HDLC, is Cisco proprietary and works only with other Cisco routers. The other option is PPP which is standards based and supported by all vendors.
QUESTION 113
What are three reasons that an organization with multiple branch offices and roaming users might implement a Cisco VPN solution instead of point-to-point WAN links? (Choose three.)
A. reduced cost
B. better throughput
C. broadband incompatibility
D. increased security
E. scalability
F. reduced latency
Answer: ADE
Explanation:
IPsec offer a number of advantages over point to point WAN links, particularly when multiple locations are involved. These include reduced cost, increased security since all traffic is encrypted, and increased scalability as s single WAN link can be used to connect to all locations in a VPN, where as a point to point link would need to be provisioned to each location.
QUESTION 114
Which two statistics appear in show frame-relay map output? (Choose two.)
A. the number of BECN packets that are received by the router
B. the value of the local DLCI
C. the number of FECN packets that are received by the router
D. the status of the PVC that is configured on the router
E. the IP address of the local router
Answer: BD
Explanation:
Sample “show frame-relay map” output:
R1#sh frame mapSerial0/0 (up): ip 10.4.4.1 dlci 401(0x191,0x6410), dynamic,broadcast,, status defined, activeSerial0/0 (up): ip 10.4.4.3 dlci 403(0x193,0x6430), dynamic,broadcast,, status defined, activeSerial0/0 (up): ip 10.4.4.4 dlci 401(0x191,0x6410), static,CISCO, status defined, active
QUESTION 115
Which command allows you to verify the encapsulation type (CISCO or IETF) for a Frame Relay link?
A. show frame-relay lmi
B. show frame-relay map
C. show frame-relay pvc
D. show interfaces serial
Answer: B
Explanation:
When connecting Cisco devices with non-Cisco devices, you must use IETF4 encapsulation on both devices. Check the encapsulation type on the Cisco device with the show frame-relay map exec command.
QUESTION 116
It has become necessary to configure an existing serial interface to accept a second Frame Relay virtual circuit. Which of the following procedures are required to accomplish this task? (Choose three.)
A. Remove the IP address from the physical interface.
B. Encapsulate the physical interface with multipoint PPP.
C. Create the virtual interfaces with the interface command.
D. Configure each subinterface with its own IP address.
E. Disable split horizon to prevent routing loops between the subinterface networks.
F. Configure static Frame Relay map entries for each subinterface network.
Answer: ACD
Explanation:
For multiple PVC’s on a single interface, you must use subinterfaces, with each subinterface configured for each PVC. Each subinterface will then have its own IP address, and no IP address will be assigned to the main interface.
QUESTION 117
What occurs on a Frame Relay network when the CIR is exceeded?
A. All TCP traffic is marked discard eligible.
B. All UDP traffic is marked discard eligible and a BECN is sent.
C. All TCP traffic is marked discard eligible and a BECN is sent.
D. All traffic exceeding the CIR is marked discard eligible.
Answer: D
Explanation:
Committed information rate (CIR): The minimum guaranteed data transfer rate agreed to by the Frame Relay switch. Frames that are sent in excess of the CIR are marked as discard eligible (DE) which means they can be dropped if the congestion occurs within the Frame Relay network. Note: In the Frame Relay frame format, there is a bit called Discard eligible (DE) bit that is used to identify frames that are first to be dropped when the CIR is exceeded.
QUESTION 118
Which two statements about using the CHAP authentication mechanism in a PPP link are true? (Choose two.)
A. CHAP uses a two-way handshake.
B. CHAP uses a three-way handshake.
C. CHAP authentication periodically occurs after link establishment.
D. CHAP authentication passwords are sent in plaintext.
E. CHAP authentication is performed only upon link establishment.
F. CHAP has no protection from playback attacks.
Answer: BC
Explanation:
CHAP is an authentication scheme used by Point to Point Protocol (PPP) servers to validate the identity of remote clients. CHAP periodically verifies the identity of the client by using a three-way handshake. This happens at the time of establishing the initial link (LCP), and may happen again at any time afterwards. The verification is based on a shared secret (such as the client user’s password).
QUESTION 119
What is the result of issuing the frame-relay map ip 192.168.1.2 202 broadcast command?
A. defines the destination IP address that is used in all broadcast packets on DCLI 202
B. defines the source IP address that is used in all broadcast packets on DCLI 202
C. defines the DLCI on which packets from the 192.168.1.2 IP address are received
D. defines the DLCI that is used for all packets that are sent to the 192.168.1.2 IP address
Answer: D
Explanation:
This command identifies the DLCI that should be used for all packets destined to the 192.168.1.2 address. In this case, DLCI 202 should be used.
QUESTION 120
Which PPP subprotocol negotiates authentication options?
A. NCP
B. ISDN
C. SLIP
D. LCP
E. DLCI
Answer: D
Explanation:
The PPP Link Control Protocol (LCP) is documented in RFC 1661. LPC negotiates link and PPP parameters to dynamically configure the data link layer of a PPP connection. Common LCP options include the PPP MRU, the authentication protocol, compression of PPP header fields, callback, and multilink options.
If you want to pass the Cisco 200-120 Exam sucessfully, recommend to read latest Cisco 200-120 Dump full version.

![clip_image001[4] clip_image001[4]](http://examgod.com/l2pimages/Free2014LatestCisco200120Dump101110Downl_9CCE/clip_image0014_thumb.jpg)
![clip_image001[8] clip_image001[8]](http://examgod.com/l2pimages/Free2014LatestCisco200120Dump91100Downlo_9BF6/clip_image0018_thumb.jpg)

![clip_image002[4] clip_image002[4]](http://examgod.com/l2pimages/Free2014LatestCisco200120Dump5160Downloa_A5C4/clip_image0024_thumb.jpg)
![clip_image001[5] clip_image001[5]](http://examgod.com/l2pimages/Free2014LatestCisco200120Dump2130Downloa_E212/clip_image0015_thumb.jpg)
![clip_image001[7] clip_image001[7]](http://examgod.com/l2pimages/Free2014LatestCisco200120Dump2130Downloa_E212/clip_image0017_thumb.jpg)